
Encryption technology allows organizations to safeguard their private information
Collaboration is crucial during times of disaster. Maintaining privacy while collaborating, however, presents a challenge. SRI International is working to solve this problem through DARPA Brandeis PRIME (privacy-preserving information mediation for enterprises). In this project, SRI employs state-of-the-art encryption technology to enable organizations to use private information without sharing it. In this way, teams can effectively collaborate while preserving confidentiality.
Disaster relief — how to enable a team effort?
When disaster strikes, organizations often work together to provide relief. Coalitions are formed that may include local, regional and national governments, along with humanitarian aid organizations and other NGOs (non-government organizations). Emergency-response coordinators must deal with countless variables when distributing people, equipment and supplies. They need to consider such questions as: Which organizations have air transport? Are the local runways long enough for that type of plane? Which organizations can provide trucks and other transportation? Who has fuel for the trucks? Can the roads handle heavy trucks, or are smaller ones needed? What kind of equipment and supplies are needed, and which organizations can supply these?
Such information is critical to formulating a cohesive response, but the need to protect sensitive information can hinder relief efforts. For example, regulations may impose safeguards on protecting individuals’ identity and health records. An aid organization may have to divide its resources among several groups and may not want them to know how they are being divided. Nations may be reluctant to share information about their supplies, capacity or assets. How can diverse groups coordinate while keeping sensitive information private?
Using information without revealing it
Dr. Karen Myers is the principal investigator for this project, a collaboration between SRI’s Artificial Intelligence Center and Computer Science Laboratory. Historically, privacy safeguards have been “all or nothing,” leading organizations to adopt a cautious position of not sharing information at all. The net result is less effective collaboration. Dr. Myers explains that her team sought to address the question: “how can we enable collaboration without directly exposing private information?”
This goal may seem impossible; how can different countries agree on delivering aid to islands in the aftermath of a hurricane without revealing their assets and capabilities? Exchanging sensitive information seems necessary to devise a viable solution.
The key to solving this challenge is Secure Multi-Party Computation (MPC). The figure below shows how MPC works — information from the participating organizations is encrypted before being shared, remains encrypted during the computation and only the final results are revealed. For example, after a natural disaster, countries might want to provide critical medical supplies but do not wish to disclose their assets and transport capabilities. With MPC, this vital information would be encrypted before sharing it with an algorithm that would determine the optimal allocation of all available resources. Since the data remains encrypted, organizations can share accurate data while ensuring that it remains private.
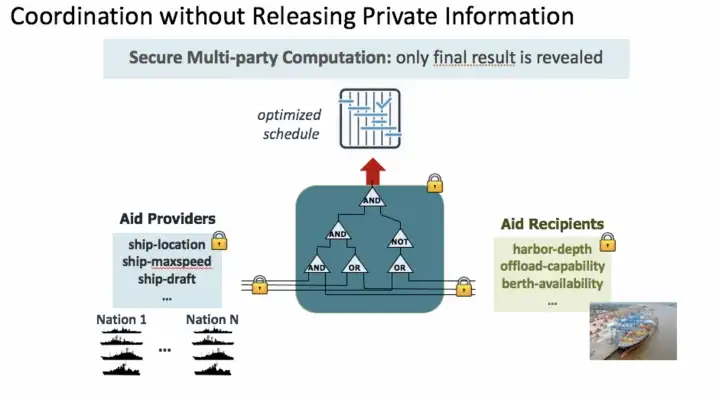
Secure Multi-party Computation: only final result is revealed
Tailoring privacy protection
Another real-world challenge addressed by this project is collaboration with tools such as documents and spreadsheets, while only sharing specific information with specific collaborators. This is currently done by making a copy of the document for each recipient and tailoring it to provide only the information that is safe to share with each specific person or organization. This process can be error-prone and time-consuming, however, and these problems are further amplified when documents need to be updated frequently.
SRI has devised an elegant solution to this problem: a collection of privacy add-ins for Microsoft Office. These add-ins enable selective access to content within Word documents and Excel spreadsheets, controlled by easily specified user policies. These policies are defined in terms of user attributes based on the privacy needs of a particular application. For example, user attributes could be defined by the organization to which an individual belongs, their functional role or their level of security access. These attributes can then be used to create tailored cryptographic keys that embed permissions for their owners. Content is encrypted so that it can be decrypted only by keys with the appropriate attributes.
For example, a Word document could be marked to reflect that different paragraphs require specific attributes to be able to view them. The privacy add-in would parse the document and then automatically encrypt each paragraph according to its marking. When the document is decrypted, the users will see only the paragraphs permitted by the attributes in their individual keys, as shown in the figure below. This technology allows an author to create a single document that can be distributed to all viewers. The attribute-based keys ensure that viewers see only the information that the author wants them to see.
This research was developed with funding from the Defense Advanced Research Projects Agency (DARPA). The views, opinions and/or findings expressed are those of the author and should not be interpreted as representing the official views or policies of the Department of Defense of the U.S. Government.
Why Brandeis? In 1888, Kodak introduced the first easy-to-use box camera. With this technology, anyone could take pictures of anything, which had not been possible with the old, bulky, wet-plate cameras. Many saw these new snapshots as a threat to privacy, and “camera fiends” were banned from beaches and other public areas.
Louis Brandeis was an up-and-coming lawyer when he wrote the influential essay, “The Right to Privacy.” He was motivated, in part, by Kodak’s invention. The essay encouraged legislators and judges to establish the right to privacy of ordinary individuals — something that we take for granted today. Brandeis was later appointed to the Supreme Court.
Collaboration is important but has traditionally required parties to reveal information that they might prefer to keep private. Concern over privacy is well-placed given that sharing, even if highly desired, results in a loss of control over what happens with the information downstream. The work by SRI International on the Brandeis PRIME project shows how groups can collaborate without revealing sensitive information, opening the door to greater cooperation amongst organizations on tasks that involve private data.



